Growing Awareness of Data Privacy
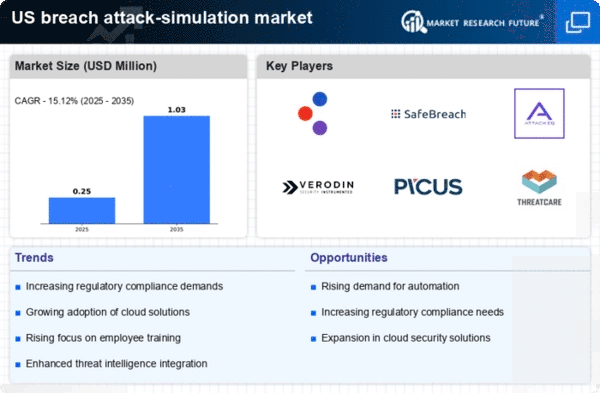
The breach attack-simulation market is significantly influenced by the growing awareness of data privacy among consumers and businesses. With increasing incidents of data breaches, organizations are compelled to prioritize data protection. In 2025, it is projected that 70% of consumers will choose to engage with companies that demonstrate robust data protection practices. This shift in consumer behavior is prompting businesses to adopt breach attack-simulation solutions to ensure compliance with data protection regulations and to build trust with their customers. As a result, the market for these simulation tools is likely to expand as organizations seek to mitigate risks associated with data breaches.
Advancements in Technology and Automation
Technological advancements and automation are driving the breach attack-simulation market forward. The integration of machine learning and artificial intelligence into simulation tools enhances their effectiveness, allowing for more realistic attack scenarios. In 2025, it is anticipated that the market for AI-driven cybersecurity solutions will reach $30 billion, indicating a strong trend towards automation in security practices. Organizations are increasingly recognizing the value of automated breach attack-simulation tools, which can provide continuous assessments and real-time insights into their security vulnerabilities. This trend suggests a shift towards more sophisticated and efficient security measures in the breach attack-simulation market.
Increasing Cybersecurity Threat Landscape
The breach attack-simulation market is experiencing growth due to the escalating cybersecurity threat landscape. Organizations are increasingly targeted by sophisticated cybercriminals, leading to a heightened demand for proactive security measures. In 2025, it is estimated that cybercrime will cost businesses globally over $10 trillion annually, prompting companies to invest in breach attack-simulation solutions. These tools allow organizations to simulate attacks, identify vulnerabilities, and enhance their security posture. As threats evolve, the need for continuous testing and improvement in security measures becomes paramount, driving the adoption of breach attack-simulation technologies across various sectors.
Shift Towards Proactive Security Strategies
The breach attack-simulation market is witnessing a shift towards proactive security strategies among organizations. Traditionally, many companies adopted reactive measures, addressing security incidents after they occurred. However, there is a growing recognition of the importance of preemptive action. In 2025, it is projected that 60% of organizations will prioritize proactive security measures, including breach attack-simulation, to identify and mitigate vulnerabilities before they can be exploited. This shift indicates a fundamental change in how organizations approach cybersecurity, driving the demand for innovative simulation tools that can effectively prepare them for potential threats.
Regulatory Pressures and Compliance Requirements
The breach attack-simulation market is also shaped by regulatory pressures and compliance requirements. As governments and regulatory bodies implement stricter data protection laws, organizations are compelled to adopt comprehensive security measures. In 2025, it is expected that compliance-related spending in the cybersecurity sector will exceed $15 billion. This regulatory environment drives the demand for breach attack-simulation solutions, as organizations seek to demonstrate compliance and avoid hefty fines. The need for regular security assessments and simulations to meet these requirements is likely to propel the growth of the breach attack-simulation market.