Rising Cyber Threat Landscape
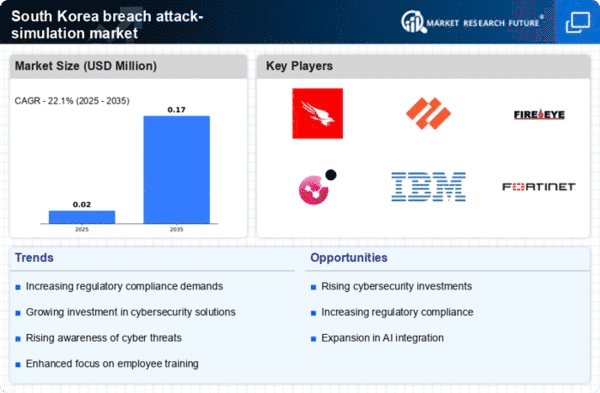
The breach attack-simulation market is experiencing growth due to the escalating cyber threat landscape in South Korea. With a notable increase in cyberattacks, organizations are compelled to adopt proactive measures to safeguard their digital assets. Reports indicate that cybercrime costs in South Korea reached approximately $1.2 billion in 2023, highlighting the urgency for effective security solutions. As businesses recognize the potential financial and reputational damage from breaches, the demand for breach attack-simulation services is likely to rise. This market driver emphasizes the necessity for organizations to simulate potential attacks, thereby enhancing their preparedness and response strategies. Consequently, the breach attack-simulation market is positioned to expand as companies seek to mitigate risks associated with evolving cyber threats.
Growing Awareness of Security Posture
In South Korea, there is a growing awareness among organizations regarding the importance of maintaining a robust security posture. This awareness is driving the demand for breach attack-simulation market solutions, as companies strive to identify vulnerabilities before they can be exploited. A survey conducted in 2025 revealed that 78% of IT decision-makers in South Korea consider breach simulations essential for their cybersecurity strategy. This trend indicates a shift towards proactive security measures, where organizations prioritize understanding their weaknesses through simulated attacks. As awareness continues to grow, the breach attack-simulation market is expected to flourish, providing businesses with the tools necessary to enhance their security frameworks and protect sensitive information.
Technological Advancements in Cybersecurity
The breach attack-simulation market is benefiting from rapid technological advancements in cybersecurity tools and methodologies. Innovations such as artificial intelligence and machine learning are being integrated into simulation platforms, allowing for more realistic and effective testing of security measures. In South Korea, the cybersecurity market is projected to reach $3 billion by 2026, driven by the adoption of advanced technologies. These advancements enable organizations to conduct comprehensive simulations that mimic sophisticated attack vectors, thereby improving their overall security posture. As technology continues to evolve, the breach attack-simulation market is likely to see increased investment and interest from businesses aiming to stay ahead of potential threats.
Regulatory Pressures and Compliance Requirements
Regulatory pressures are significantly influencing the breach attack-simulation market in South Korea. With the introduction of stringent data protection laws, organizations are required to demonstrate compliance through regular security assessments. The Personal Information Protection Act (PIPA) mandates that companies implement adequate security measures to protect personal data, which includes conducting breach simulations. As a result, businesses are increasingly turning to breach attack-simulation services to ensure compliance and avoid hefty fines. This regulatory landscape is expected to drive growth in the breach attack-simulation market, as organizations seek to align their security practices with legal requirements and enhance their overall risk management strategies.
Increased Focus on Incident Response Preparedness
The breach attack-simulation market is also being propelled by an increased focus on incident response preparedness among organizations in South Korea. As cyber threats become more sophisticated, companies are recognizing the need for effective incident response plans. Simulating breaches allows organizations to test their response capabilities and identify areas for improvement. A recent study indicated that 65% of South Korean firms have implemented breach simulations as part of their incident response strategy. This trend underscores the importance of preparedness in mitigating the impact of cyber incidents. Consequently, the breach attack-simulation market is likely to expand as businesses prioritize enhancing their incident response frameworks and resilience against potential attacks.