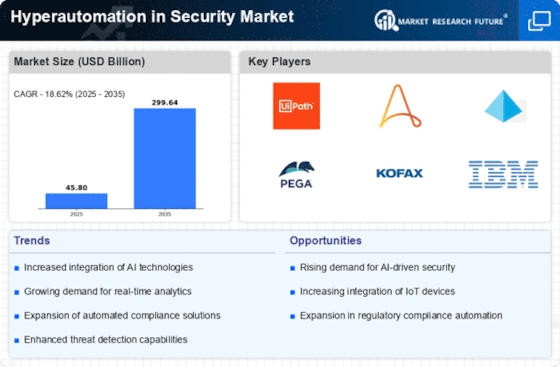
Market Share
Hyperautomation in Security Market Share Analysis
Hyperautomation, which blends sophisticated automation technology with security procedures to improve threat detection, response, and cybersecurity resilience, is changing the security market. AI and ML in security operations are a major trend in security hyperautomation. These technologies allow security systems to analyze massive volumes of data in real time, find patterns, and spot abnormalities that may suggest security vulnerabilities. Hyperautomation with AI and ML improves threat detection, helping enterprises stay ahead of developing cyberthreats.
Automating incident response and vulnerability management is another trend. Hyperautomation lets security teams focus on more complicated and strategic responsibilities by automating repetitive security operations. Rapid detection and mitigation of security issues using automated incident response systems reduces response times and cyber dangers. This trend improves operational efficiency and security scalability in the face of escalating cybersecurity threats.
Security orchestration, automation, and response (SOAR) technologies are integrated during security market hyperautomation. SOAR platforms simplify incident response using security tools and technology. SOAR platform automation processes may examine security alarms, analyze threat data, and coordinate responses. This development improves security operations, allowing firms to quickly respond to cyber attacks and manage risks.
The market is also seeing RPA integration in security operations. RPA automates rule-based and repetitive processes including log analysis, compliance checks, and security audits. These processes may be automated to increase accuracy, eliminate human error, and maintain security and regulatory compliance. The security industry's focus on balancing human knowledge and machine efficiency in cybersecurity concerns is reflected in RPA integration.
Additionally, security hyperautomation is meeting threat intelligence automation needs. Organizations use automation to acquire, evaluate, and share threat intelligence in real time. Security teams may proactively improve their security by receiving automated threat intelligence feeds regarding the newest cyber threats, vulnerabilities, and attack methods. Cybersecurity is dynamic, thus timely threat intelligence is essential for defensive measures.














Leave a Comment