Market Analysis
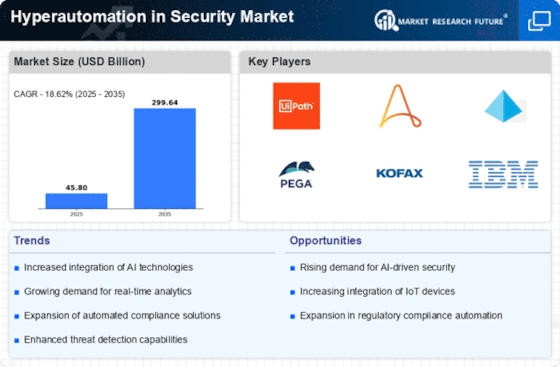
In-depth Analysis of Hyperautomation in Security Market Industry Landscape
Hyperautomation—a strong combo of AI, ML, and RPA—is transforming the security environment. Several market drivers drive security hyperautomation adoption and influence.
One reason is the sophistication of cyber attacks and the need for stronger and more adaptable protection. Traditional security solutions typically fall behind cybercriminals' techniques. Hyperautomation uses AI and ML algorithms to analyze massive volumes of data, find patterns, and discover abnormalities in real time. This dynamic and proactive strategy improves security threat detection and response.
Many businesses are overburdened by security warnings and incidents, causing alert fatigue and delayed reaction times. Hyperautomation automates repetitive operations and decision-making. Automation may speed up data analysis, threat detection, and incident response, letting security staff focus on more complicated and strategic cybersecurity activities.
IT complexity and diversified technology adoption drive security hyperautomation. Modern companies use multi-cloud environments, many apps, and several technologies. Hyperautomation streamlines IT security and helps enterprises manage complicated IT ecosystems. This comprehensive approach helps security teams find vulnerabilities and threats across systems and apps.
Compliance and regulatory criteria also drive security hyperautomation. Many sectors must follow strict data privacy laws. Hyperautomation automates data monitoring, access control, and incident reporting for compliance. This decreases regulatory fines and gives firms the tools to confirm industry standards compliance.
Cost efficiency influences security hyperautomation adoption. The initial investment in hyperautomation systems may be high, but the long-term benefits, such as lower operating costs, efficiency gains, and security, make it worthwhile. Cybersecurity management is cheaper when regular security duties can be automated and hazards can be addressed quickly.
Organizations worldwide deal with a cybersecurity skills gap. Hyperautomation fills the talent gap by automating non-specialized jobs, allowing security teams to focus on high-value duties. Organizations must enhance human skills with automation to address cyber threats in a highly qualified cybersecurity professional market.
Hyperautomation is also driven by cyber threats' dynamic nature and real-time reaction needs. Automatic threat detection and response let firms respond quickly to security problems, reducing cyberattack damage. Hyperautomation's speed and precision reduce threats' dwell time in an organization's network, improving cybersecurity resilience.
Collaboration and integration are key to security hyperautomation. Hyperautomation solutions can interface with security infrastructure and tools to create a single security ecosystem. Organizations may use hyperautomation and their security technology investments thanks to this compatibility."














Leave a Comment