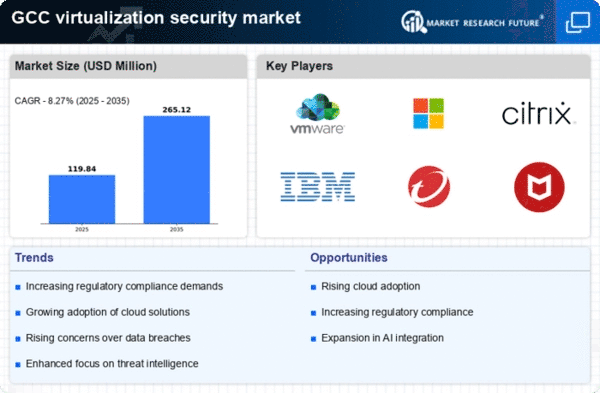
GCC Virtualization Security Market Segment Insights
Virtualization Security Market Deployment Type Insights
The Deployment Type segment of the GCC Virtualization Security Market plays a crucial role in shaping the landscape of virtualization security in the region. With the rising necessity to secure virtualized environments, organizations in the GCC are increasingly evaluating various deployment options to meet their specific needs. The on-premises approach remains popular among enterprises that prioritize complete control over their security infrastructure and data, enabling them to customize security measures according to their unique organizational requirements.This segment often appeals to industries such as government and finance, where regulatory compliance and data sovereignty are paramount concerns.
On the other hand, the Cloud-Based deployment type is gaining traction due to its flexibility, scalability, and cost-effectiveness. Organizations are drawn to cloud-based solutions for their ability to quickly adapt to changing demands without heavy capital expenditure, making them attractive to small and medium-sized businesses in the GCC that are looking to enhance their security posture without significant upfront costs.Additionally, the Hybrid deployment type combines the strengths of both On-Premise and Cloud-Based solutions, allowing organizations to maintain sensitive data on-site while leveraging cloud capabilities for less critical applications. This flexibility helps businesses effectively manage their security assets across diverse environments. The demand for robust virtualization security frameworks in the GCC is driven by the increasing frequency of cyber threats, reliance on digital transformation, and the growing adoption of cloud infrastructures.
Consequently, organizations are prioritizing investments in virtualization security solutions tailored to their deployment preferences, thus influencing the GCC Virtualization Security Market segmentation significantly. As the region continues to embrace technological advancements, it is evident that these deployment types will play a vital role in ensuring enterprises can effectively safeguard their digital assets while navigating the complexities of the ever-evolving threat landscape. Through strategic implementation of these deployment types, organizations in the GCC can foster a secure digital environment, enhancing operational efficiency and facilitating compliance with local regulations.
The market statistics indicate that the focus on virtualization security deployment types is expected to grow, driven by an increasing understanding of their importance for safeguarding critical infrastructure and sensitive information against various cyber threats. Overall, the Deployment Type segment presents diverse opportunities for growth within the GCC Virtualization Security Market, paving the way for innovative solutions and advancements in security measures.
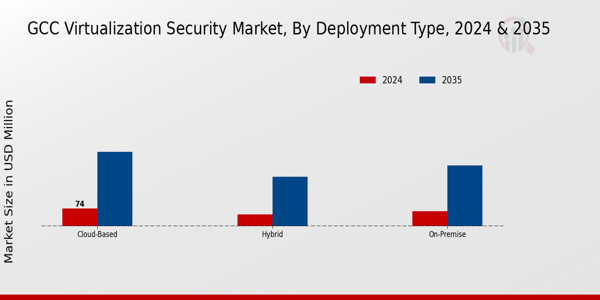
Source: Primary Research, Secondary Research, MRFR Database and Analyst Review
Virtualization Security Market Component Insights
The GCC Virtualization Security Market is experiencing significant growth, particularly within the Component segment, which comprises Solutions, Services, and Software. This region has become increasingly aware of the need for robust virtualization security measures due to a surge in cyber threats and vulnerabilities associated with virtualization technologies. The Solutions aspect is pivotal as organizations seek advanced protection techniques, including access control and encryption, to safeguard virtual environments.
Meanwhile, the Services component remains crucial; consulting and implementation services support organizations in maintaining compliance and securing their virtual assets effectively.The Software portion serves as a backbone for automation and monitoring, enabling real-time threat detection and mitigation. The demand for these Components is driven by industrial growth and a greater emphasis on digital transformation within the GCC countries, as governments increasingly prioritize cybersecurity initiatives to protect critical infrastructure and sensitive data. This dynamic landscape offers numerous opportunities for vendors to innovate and provide tailored solutions that address the unique challenges faced by various industries in the region, thus reinforcing their market presence.
Virtualization Security Market Vertical Insights
The GCC Virtualization Security Market is diversified across several important verticals, with each segment contributing significantly to the overall landscape. The Healthcare sector relies heavily on virtualization security due to the sensitivity of patient data and the need for robust compliance with data protection regulations. In Financial Services, the demand for secure transactions and protection against fraud drives the implementation of advanced virtualization security solutions, ensuring financial institutions can safeguard client information effectively.The Information Technology sector stands as a crucial player, necessitating high levels of security for virtualized environments to mitigate risks associated with cyber threats.
Retailers are increasingly adopting virtualization for operational efficiency, where the integration of security solutions protects customer data and minimizes the risk of breaches. The Government sector, focused on safeguarding national security and citizen information, prioritizes virtualization security to enhance resilience against cyber attacks. Overall, these verticals highlight the critical need for tailored virtualization security solutions in the GCC region, reflecting the growing awareness of the importance of data security across various industries.As digital transformation accelerates, so does the urgency for comprehensive virtualization security measures to address emerging threats and enhance business continuity.
Virtualization Security Market Security Type Insights
The GCC Virtualization Security Market is increasingly shaped by its categorization into various Security Types, which play a crucial role in enhancing overall cybersecurity measures across the region. Data Security is vital for ensuring that sensitive information remains protected against breaches, driven by rising concerns about data privacy amidst stringent regulations. Network Security, on the other hand, safeguards the integrity and usability of network resources, which is particularly significant given the growing number of cyber threats targeting the GCC infrastructure.Application Security addresses vulnerabilities in software deployments, ensuring that applications within virtualized environments are not exploited.
Endpoint Security is critical as the proliferation of remote work has expanded the attack surface, necessitating robust defenses for devices accessing corporate networks. Each of these segments represents a growing area of focus as organizations in the GCC look to bolster their cybersecurity frameworks, reflecting broader trends within the GCC Virtualization Security Market and driving a notable shift towards more comprehensive and integrated security solutions.These diverse segments together contribute significantly to improving the quality of security measures in a rapidly evolving digital landscape.