Market Analysis
In-depth Analysis of Security Software Telecom Market Industry Landscape
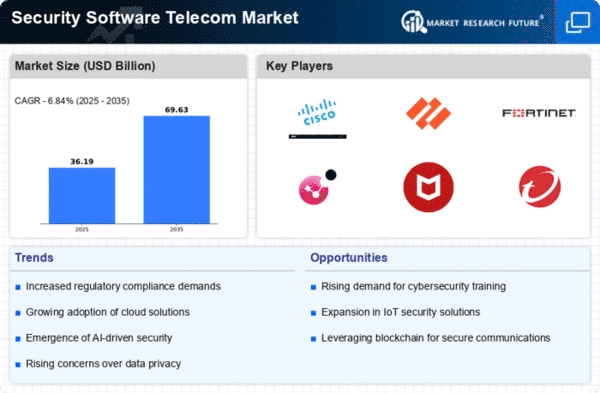
The market dynamics of security software in the telecom industry are shaped by a variety of factors, including evolving cyber threats, regulatory requirements, technological advancements, and competitive pressures. Security software plays a crucial role in safeguarding telecom networks, systems, and data from unauthorized access, malicious attacks, and data breaches. One of the key drivers of market dynamics in this sector is the increasing frequency and sophistication of cyber threats targeting telecommunications infrastructure and services. As telecom networks become more interconnected and reliant on digital technologies, they become vulnerable to a wide range of cyber attacks, including malware, phishing scams, DDoS (Distributed Denial of Service) attacks, and insider threats.
Technological innovation drives the adoption and evolution of security software in the telecom market. Advancements in artificial intelligence, machine learning, and predictive analytics enable telecom operators to detect and respond to security threats in real-time, enhancing their ability to proactively identify and mitigate risks. Additionally, the proliferation of IoT (Internet of Things) devices and 5G networks introduces new security challenges and complexities, prompting telecom operators to invest in advanced security solutions capable of securing diverse endpoints and mitigating emerging threats.
Moreover, regulatory requirements and compliance mandates exert a significant influence on the market dynamics of security software in the telecom industry. Governments and regulatory bodies impose stringent regulations and standards to ensure the security, privacy, and integrity of telecom networks and customer data. Telecom operators must adhere to these regulations, such as GDPR (General Data Protection Regulation) in Europe and HIPAA (Health Insurance Portability and Accountability Act) in the United States, by implementing robust security measures, conducting regular audits, and reporting security incidents.
Furthermore, the competitive landscape of the telecom industry drives the market dynamics of security software as operators vie for market share and seek to differentiate themselves through superior security capabilities. Security has become a key differentiator for telecom operators, particularly in enterprise and business markets where customers prioritize data protection and risk management. By investing in best-in-class security software solutions, telecom operators can enhance their reputation, build trust with customers, and gain a competitive edge in the marketplace.
However, despite the increasing emphasis on security, telecom operators face challenges in implementing and maintaining effective security measures. One challenge is the complexity and scale of telecom networks, which encompass a vast array of interconnected systems, devices, and protocols. Securing these networks requires a holistic approach that addresses vulnerabilities at every layer of the infrastructure, from the core network to edge devices and endpoints.
Additionally, the evolving nature of cyber threats requires telecom operators to continuously update and adapt their security strategies to address emerging risks. This requires ongoing investment in research and development, threat intelligence, and security awareness training to stay ahead of cybercriminals and protect against evolving threats. Moreover, telecom operators must strike a balance between security and usability, ensuring that security measures do not unduly impact network performance or user experience.















Leave a Comment