Top Industry Leaders in the Security Advisory Services Market

Competitive Landscape of Security Advisory Services Market: Navigating the Labyrinth
The Security Advisory Services Market is a dynamic and rapidly evolving space, fueled by the ever-escalating cyber threats across industries. Organizations, big and small, are increasingly turning to professional advisors for help in navigating the complex world of cybersecurity. This has given rise to a diverse and competitive landscape, with established players battling it out alongside nimble newcomers for a slice of the lucrative pie.
Key Players:
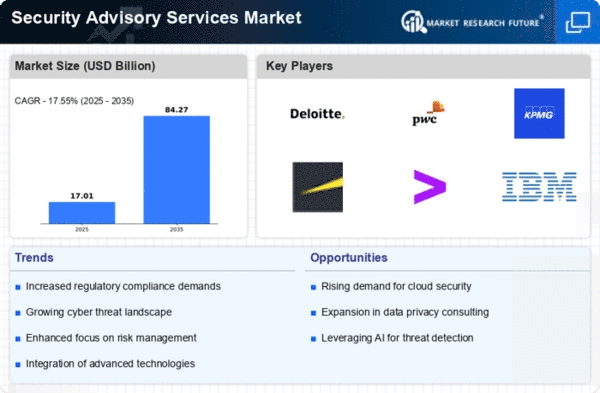
- Deloitte Touche Tohmatsu Limited (US)
- Ernst & Young Global Limited (UK),
- KPMG International Cooperative (Netherlands)
- PricewaterhouseCoopers Private Limited (UK)
- Coalfire Systems, Inc. (US)
- CybeRisk (US), Cisco Systems, Inc. (US)
- Tata Consultancy Services Limited (India
- eSentire, Inc. (Canada)
- Security Compass (Canada)
- Novacoast, Inc. (US)
- Kudelski Security (Switzerland)
- DXC Technology Company (US)
- Rapid7 LLC (US)
- Intertek Group PLC (UK)
Strategies Adopted:
Players in this competitive landscape are vying for market share through a variety of strategies. Here are some notable trends:
-
Specialization: Firms are carving out niches based on specific industry expertise, threat types, or service offerings, such as cloud security or GDPR compliance consulting.
-
Partnerships and Acquisitions: Collaborations with technology vendors and acquisitions of smaller players are accelerating, enabling a broader range of services and deeper market penetration.
-
Innovation: Development of proprietary tools and platforms for vulnerability detection, threat analysis, and security automation is key to differentiation.
-
Data-Driven Insights: Leveraging AI and machine learning for threat intelligence, risk prediction, and proactive security recommendations is becoming increasingly crucial.
-
Global Expansion: Established players are expanding their geographic footprint to cater to the rising demand for security advisory services in emerging markets.
Factors for Market Share Analysis:
Assessing market share in this dynamic landscape requires a nuanced approach. Key factors to consider include:
-
Service Portfolio Breadth and Depth: The diversity and expertise of offered services across different security domains play a crucial role.
-
Client Focus and Industry Specialization: Catering to specific industry needs and demonstrating deep domain knowledge attracts particular client segments.
-
Geographical Reach and Market Penetration: Global presence and established local connections prove advantageous in capturing market share.
-
Brand Reputation and Client Testimonials: Trust and established track record in handling complex security challenges influence client choice.
-
Technology Innovation and Investment: Continuous development of cutting-edge tools and platforms keeps firms ahead of the curve.
New and Emerging Companies:
Several new and emerging companies are disrupting the market with innovative offerings and agile approaches. Some noteworthy examples include:
-
Volexity: This threat intelligence firm provides unique insights into attacker profiles and tactics, empowering organizations to anticipate and combat evolving threats.
-
Randori: Offering innovative penetration testing and adversary simulation services, Randori helps organizations identify and address critical security vulnerabilities before attackers exploit them.
-
Deepwatch: Specializing in cloud security, Deepwatch utilizes AI and machine learning to continuously monitor and analyze cloud environments for potential threats.
-
Cybereason: This endpoint security provider differentiates itself with an intuitive platform that uses behavioral analysis to detect and thwart sophisticated cyberattacks.
Current Company Investment Trends:
Security advisory service providers are actively investing in various areas to strengthen their market position and cater to evolving client needs. Key trends include:
-
Security Automation and Orchestration (SOAR) Platforms: Investing in automated incident response and threat hunting tools to improve efficiency and effectiveness.
-
Cloud Security Expertise: Building capabilities to address the unique security challenges of cloud adoption and migration.
-
Threat Intelligence Platforms: Developing proprietary platforms for real-time threat analysis and sharing, providing actionable insights to clients.
-
Talent Acquisition and Training: Attracting and retaining top cybersecurity professionals with specialized skills and experience.
-
Research and Development: Continuously investing in research to stay ahead of emerging threats and develop innovative security solutions.
Latest Company Updates:
-
Oct 27, 2023: McAfee acquires consulting firm wellington turtell: This acquisition strengthens McAfee's cybersecurity advisory services portfolio. -
Nov 15, 2023: Palo Alto Networks launches new threat detection and response service: This service leverages the company's Cortex XDR platform to provide real-time threat detection and incident response capabilities. -
Dec 05, 2023: Accenture acquires cybersecurity firm Mandiant: This acquisition expands Accenture's cybersecurity offerings and positions it as a leader in incident response and forensics.