Top Industry Leaders in the Intelligent Threat Security Market

Competitive Landscape of Intelligent Threat Security Market:
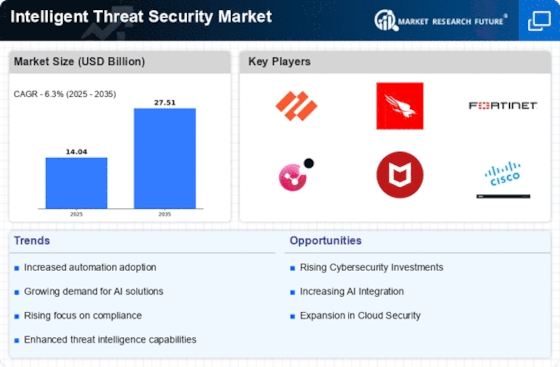
The Intelligent Threat Security market is experiencing explosive growth fueled by the ever-evolving threat landscape. Organizations are desperately seeking solutions that go beyond traditional static defense mechanisms and leverage AI, machine learning, and automation to proactively counter sophisticated cyberattacks. This dynamic market fosters fierce competition, with established players jockeying for position alongside agile startups brimming with innovative ideas.
Key Players:
- RealCISCO
- SentinelOne Inc.
- Anomali Inc.
- Microsoft
- IBM Corporation
- Dell Inc.
- CrowdStrike Inc.
- Check Point Software Technologies
- Huawei Technologies
- Fortinent Inc.
- Vmware Inc.
Factors Influencing Market Share Analysis:
- Technology Leadership: Continuous innovation in AI, machine learning, and automation differentiates leading players. Superior threat detection and prevention capabilities, accurate threat intelligence collection and analysis, and effective automated response mechanisms are key metrics for gauging technology leadership.
- Product Portfolio Breadth: Offering a comprehensive suite of ITS solutions covering endpoints, networks, cloud environments, and identities is crucial. Vendors with integrated platforms that provide unified visibility and control tend to gain an edge.
- Global Reach and Market Presence: Established players with extensive global networks and customer support infrastructures hold an advantage, particularly in catering to large multinational organizations. However, nimble startups can bridge the gap by adopting flexible deployment models like SaaS and leveraging strategic partnerships.
- Pricing and Licensing Models: Competitive pricing strategies and flexible licensing options tailored to different deployment scenarios and industry verticals are essential for attracting diverse customer segments. Offering subscription-based models and freemium tiers for specific features can create entry points for budget-conscious organizations.
New and Emerging Companies:
- IoT Security Specialists: With the proliferation of connected devices, startups like Armis and CyberMDX are addressing the unique security challenges of the IoT landscape. Their solutions provide vulnerability management, threat detection, and incident response specifically tailored for IoT ecosystems.
- Behavioral Detection and Deception Technologies: Companies like Darktrace and Deepwatch are leveraging advanced behavioral analytics and deception techniques to identify anomalous activity and lure attackers into revealing their tactics. These AI-powered solutions offer a proactive approach to threat detection, supplementing traditional signature-based methods.
- Open-Source Threat Intelligence Platforms: The emergence of open-source alternatives like MISP and AlienVault OTX demonstrates the growing collaborative spirit within the cybersecurity community. These platforms facilitate threat intelligence sharing and community-driven analysis, creating a valuable resource for organizations to augment their own security capabilities.
Current Company Investment Trends:
- AI and Machine Learning: Significant investments are directed towards advanced AI and machine learning algorithms to enhance threat detection accuracy, automate incident response, and predict future attack patterns.
- Threat Intelligence Integration: Merging threat intelligence feeds from various sources and streamlining their integration into security platforms is a major focus area. This involves partnerships with threat intelligence providers and developing automated data ingestion and analysis capabilities.
- Cloud-Native Security Solutions: Recognizing the shift towards cloud adoption, vendors are building and scaling cloud-based ITS offerings designed for optimal security in dynamic, distributed environments.
- Security Orchestration, Automation, and Response (SOAR): Integrating SOAR capabilities into ITS platforms is gaining traction, enabling organizations to automate incident response workflows and streamline security operations.
Latest Company Updates:
January 9, 2024, Google Cloud announces the expansion of its Chronicle security platform with new threat intelligence and incident response capabilities. This update strengthens Google Cloud's security offerings for enterprises utilizing hybrid and multi-cloud environments.
January 4, 2024, Mandiant, a leading incident response firm, unveils its Mandiant Advantage MDR service, integrating its expertise with XDR technology for comprehensive threat detection, investigation, and response. This offering caters to organizations seeking a managed approach to security.