Market Analysis
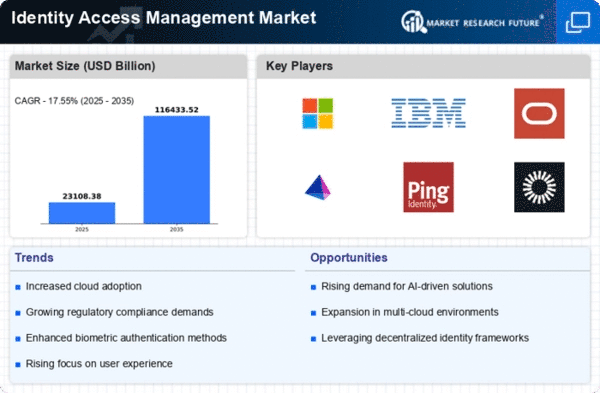
In-depth Analysis of Identity Access Management Market Industry Landscape
The Identity and Access Management (IAM) industry is changing due to network safety threats and the growing need for secure and effective access restrictions. Once a specialist, IAM is now a core aspect of many businesses. Innovative trends, administrative consistency requirements, and growing awareness of the importance of strong identification and access restrictions shape the IAM business.
IAM market aspects are driven by cutting-edge innovation enhancement. Traditional border-based security is insufficient when organizations use dispersed computers, cell phones, and IoT devices. IAM techniques are adapting to these developments, enabling more flexible validation strategies. Multifaceted verification, biometric recognition, and social examination are becoming standard IAM components, improving security and customer experience.
Administrative consistency also shapes IAM market aspects. Global legislatures and administrative authorities are approving strict information assurance and security standards. GDPR, HIPAA, and other requirements necessitate strong IAM solutions to protect sensitive data. These consistency requirements force companies to invest in IAM advancements, fueling market growth.
Additionally, increased awareness of network safety risks and information breaches have focused associations on IAM. The need for elaborate procedures to monitor customer lifestyles and identify and address security threats affects market aspects. IAM sellers are using computational reasoning and AI to identify threats and automate response tools to improve network security.
Another factor strengthening the IAM industry is global corporate activity. As associations expand globally, managing characters and access across territories and administrative circumstances becomes more complicated. IAM solutions that offer unified control and global flexibility are popular, boosting market growth to fulfill multinational enterprises' diverse needs.
The Zero Trust security approach is also affecting IAM market components. IAM systems are building continual validation and approval tools since no client or device should be trusted. This strategy aligns with the shifting concept of digital threats, focusing on protecting resources inside and beyond the traditional corporate organization.















Leave a Comment