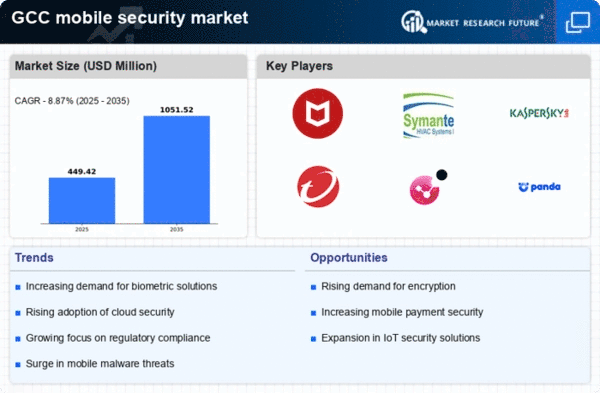
GCC Mobile Security Market Segment Insights
Mobile Security Market Solution Insights
The Solution segment of the GCC Mobile Security Market plays a crucial role in addressing the increasing demand for robust security measures in the mobile ecosystem. As businesses, government institutions, and individuals in the GCC recognize the critical importance of safeguarding their sensitive data, various solutions have emerged to fortify mobile devices against an array of security threats. Mobile Data Protection is a vital component, providing essential tools to ensure that personal and corporate data is shielded from unauthorized access and potential breaches, thus building trust in the digital landscape.
Firewall solutions serve as the first line of defense, monitoring and controlling outgoing and incoming network traffic based on predetermined security rules, thereby preventing malicious attacks and unauthorized access to mobile applications. Data Encryption is gaining significant traction as it transforms sensitive information into a secure format that is unreadable without the proper key, making it indispensable for protecting confidential communications and stored data, thus ensuring compliance with regulatory frameworks. Multi-Factor Authentication is becoming increasingly important, enhancing security by requiring multiple forms of verification to access mobile applications and services, which adds an extra layer of security amidst rising cyber threats.
Collectively, these solutions reflect the growing awareness and response to the complexities of mobile security in the GCC region, driven by factors such as an increase in mobile usage, a surge in cybercrime, and the proactive stance of regulatory bodies advocating for enhanced data protection standards. As organizations in the GCC continue to digitize their operations and embrace mobile technologies, the demand for these diverse solutions will only intensify, underpinning the need for a resilient mobile security infrastructure.
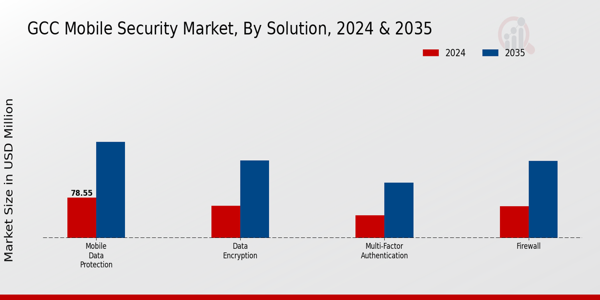
Source: Primary Research, Secondary Research, MRFR Database and Analyst Review
Mobile Security Market Deployment Insights
The Deployment segment of the GCC Mobile Security Market plays a vital role in shaping the industry's landscape. As organizations within the Gulf Cooperation Council increasingly recognize the demand for secure mobile operations, methods of deployment such as Cloud and On-Premises have emerged as key focus areas. Cloud-based solutions offer enhanced scalability and flexibility, which is essential in today's fast-paced digital environment, allowing businesses to adapt rapidly to changing security challenges. On-Premises deployment remains significant due to its control and data integrity benefits, particularly for companies with strict regulatory requirements.
The growth in mobile device usage and the increasing sophistication of cyber threats in the GCC region further drive the need for robust mobile security solutions. The GCC Mobile Security Market data reveals a strong market trajectory as companies aim to protect sensitive information and maintain customer trust, highlighting the importance of effective deployment strategies in the overall mobile security landscape. As the prevalence of cyber attacks continues to rise, organizations are prioritizing mobile security to safeguard their assets, ultimately contributing to the GCC Mobile Security Market revenue growth in the long term.
Mobile Security Market System Insights
The System segment of the GCC Mobile Security Market is evolving rapidly due to the increasing reliance on mobile devices for both personal and business use in the region. Mobile operating systems such as Windows, Android, and iOS play crucial roles in determining the overall security landscape. Android, due to its wide market penetration, is often targeted by cyber threats, making robust security measures essential, while iOS enjoys a strong reputation for security, often commanding premium performance among users, which drives demand for specialized mobile security solutions.
Windows, as a versatile platform, is making inroads into mobile security to address enterprise needs. Governments in the GCC region are also heavily investing in cybersecurity enforcement initiatives, further emphasizing the importance of securing these operating systems against evolving threats. The growth drivers in this segment include an upswing in mobile transactions and the proliferation of IoT devices. However, challenges remain, such as the lack of awareness about mobile security and the sophistication of cyber threats. Overall, this System segment reflects a highly strategic aspect of the GCC Mobile Security Market, with potential for significant development and investment in security solutions to safeguard mobile environments.
Mobile Security Market End-User Insights
The End-User segment of the GCC Mobile Security Market plays a pivotal role in shaping market dynamics across various industries. Telecom and IT sectors remain critical as they drive mobile security adoption due to increasing connectivity and data exchange, necessitating robust security solutions. Individual Users are becoming more aware of mobile threats, pushing demand for personal security applications. The BFSI sector, being highly regulated, emphasizes the need for compliance and secure transactions, leading to a surge in security investments.Government entities prioritize mobile security to safeguard sensitive data and to maintain public trust, especially in digital initiatives.
In Healthcare, the protection of patient data is paramount, thus heightening the demand for advanced security services. Retail businesses face threats related to customer transactions and data breaches, while Education institutions are keen on protecting student information and facilitating secure communication channels. This diverse End-User segmentation illustrates the broad applicability and the growing need for mobile security solutions, driven by unique sector challenges and the evolving digital landscape in the GCC region.Furthermore, the acceleration of digital transformation initiatives across sectors adds to the urgency for tailored mobile security solutions that can cater to specific industry requirements.