Market Share
Threat Intelligence Management Market Share Analysis
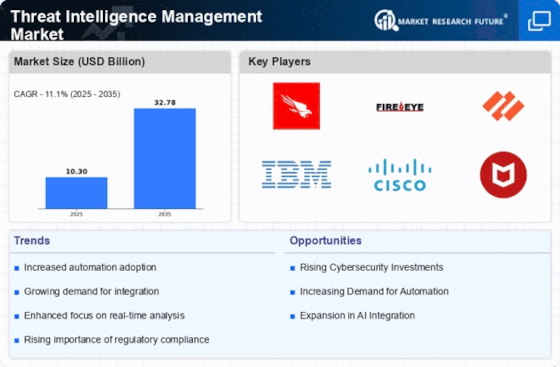
The Threat Intelligence Management market is showing strong trends as companies increase their efforts to strengthen network security in light of the ever-changing threat landscape. A key trend is the growing use of threat information to prevent digital attacks. Organizations are realizing that timely and meaningful threat intelligence may boost security. Threat intelligence management systems gather, analyze, and share intelligence to mitigate threats, reflecting a change from reactive to proactive online defense.
Threat intelligence and security are becoming commercial priorities. Organizations want secure environments where threat intelligence integrates seamlessly with SIEM frameworks, occurrence reaction stages, and other security tools. This cooperation provides comprehensive data and enables faster and more intelligent dynamic notwithstanding security events, improving online protection actions. The trend toward a unified security strategy emphasizes the need for security innovation collaboration.
Computerization is shaping Threat Intelligence Management. The daily volume of threat information challenges manual evaluation and response. Thus, organizations are using robotization and coordination in threat intelligence management solutions to better manage information. Mechanization speeds up threat detection and response and lets security teams focus on more complicated tasks, making network protection more efficient.
The expansion of threat intelligence beyond network defense is crucial. Threat intelligence now includes worldwide, industry-specific, and brand-related data in addition to malware and vulnerability data. This growing degree allows associations to interpret risks in their own risk scenarios. Thus, Threat Intelligence Management systems are improving to provide a more complete threat picture, allowing organizations to tailor their protections to specific dangers that may affect their work.
Data exchange and coordinated action in the network safety local area are becoming more important. Organizations may now share considerable threat intelligence with friends and industry partners through threat intelligence sharing platforms and consortiums. This joint approach protects against common threats and plans for internet security issues. The trend toward data sharing reflects a growing awareness of online safety and the need for a collective digital defense.
Threat Intelligence Management is shaped by threat hunting and proactive threat detection. Organizations are investing on security units to identify internal dangers. Threat intelligence and cutting-edge analysis enable proactive threat hunting, allowing companies to identify and eliminate dangers before they grow. This approach matches the wider shift toward proactive and preventive network protection.















Leave a Comment